Apricot Feature Card (Rev 1.6.1)

Interrupt Request Level (IRQ)
The daughterboard requires three IRQ's:
- PCnet-ISA+ Ethernet adapter: set by the feature BIOS Setup utility.
- Enhanced Business Audio system: set by the Windows device driver.
- SLCD CD-ROM interface: selected by a switch on the daughterboard.
| IRQ |
Typical
Assignment |
IRQ
Defaults and Options |
| PCnet-ISA+ |
Audio |
SLCD |
| IRQ0 |
System |
| IRQ1 |
Keyboard Controller |
| IRQ2 |
Slave Interrupt Controller |
| IRQ3 |
Serial Port 2 |
Option |
|
Option |
| IRQ4 |
Serial Port 1 |
Option |
|
|
| IRQ5 |
|
Option |
|
Default |
| IRQ6 |
Diskette Controller |
| IRQ7 |
Parallel Port |
|
Option |
|
| IRQ8 |
Real Time Clock |
| IRQ9 |
Video |
Option |
Option |
|
| IRQ10 |
|
Option |
Option |
|
| IRQ11 |
|
Option |
Default |
|
| IRQ12 |
Mouse |
Option |
|
|
| IRQ13 |
Coprocessor |
| IRQ14 |
Hard Disk Controller |
| IRQ15 |
|
Option |
|
|
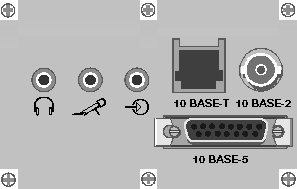
Rear View


Direct Memory Access (DMA) Channel
The daughterboard requires DMA channels for the following:
- PCnet-ISA+ Ethernet adapter: set by the feature BIOS Setup utility.
- Enhanced Business Audio system: set by the Windows device driver.
| DMA |
Typical
Assignment |
DMA
Defaults and Options |
| PCnet-ISA+ |
Audio |
| DMA0 |
|
|
Option |
| DMA1 |
|
|
Option |
| DMA2 |
Diskette/Floppy Disk Controller |
| DMA3 |
|
Option |
Option |
| DMA4 |
System |
| DMA5 |
|
Option |
|
| DMA6 |
|
Option |
|
| DMA7 |
|
Option |
|
Base Memory Address
The PCnet-ISA+ Ethernet adapter requires 32KBytes (8000h) out of the
processors address space for the RPL (Remote Program Load) code in the daughterboards
memory. The base memory address specifies where this memory begins. C8000h is used by
default; the Feature BIOS Setup utility can assign D8000h instead.
Base input/output (I/O) Port Address
PCnet-ISA+ Ethernet Adapter
The Feature BIOS Setup utility can assign any base I/O port address
between 200h and 3A0h in 20h increments.
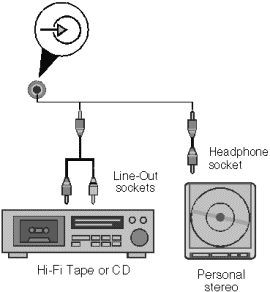
Enhanced Business Audio System
The audio system can use the I/O ports listed below, selected by a
switch on the daughterboard.
The FM synthesizer also uses 388h to 38Bh; to maintain Ad Lib
cmpatability, this cannot be altered.
SLCD CD-ROM Interface
The SLCD CD-ROM interface can use the I/O ports listed below, selected
by a switch on the daughterboard.
Jumpers and Switches
Switch Pack SW1
| SLCD Interface |
Options |
SW1 : 1 |
Enable |
ON |
Disable |
OFF |
| SLCD Interface IRQ Polarity |
Options |
SW1 : 2 |
SW1 : 3 |
Non-inverted |
ON |
OFF |
Inverted |
OFF |
ON |
| SW1 : 4 always set to off |
| Audio / SLCD Base I/O Port Addresses |
Options |
SW1 : 5 |
SW1 : 6 |
534h / 320h |
ON |
ON |
608h / 340h |
ON |
OFF |
E84h / 350h |
OFF |
ON |
F44h / 360h |
OFF |
OFF |
| SLCD IRQ |
Options |
SW1 : 7 |
SW1 : 8 |
IRQ 5 |
ON |
OFF |
IRQ 3 |
OFF |
ON |
ITALIC settings are default
SW1 Default positions
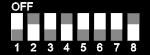
PL8
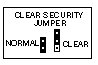
PL3

 
Quick Guide to Security
Logging-on to the computer
Changing your pasword
Logon statistics
Variations in the logon sequence
Unattended mode for Microsoft Windows
 
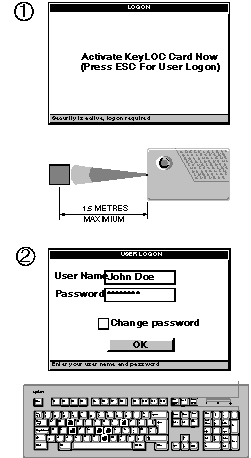
Logging-on to the
computer
Every time you turn on or restart the computer you can expect to go
through a logon sequence. This typically involves an infrared device called a KeyLOC
card, a user name and a password.
 
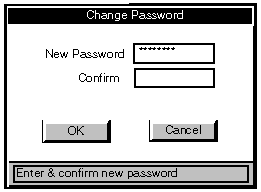
Changing your password
After typing your user name and password in the User Logon dialog box,
select the Change Password check box before choosing OK. The Change Password dialog box
appears.
Type a new password in the New Password text box, and repeat it in the Confirm text box. A
password can have up to eight characters, selected from A-Z, a-z, 0-9 and space. The
security system may enforce a minimum password length
Choose the OK button to make the change, or Cancel to keep your existing password. Any
change you make will come into effect when you next logon.
 
Logon statistics
When you logon, some logon statistics are displayed, for example:
No of valid logons 11, last valid logon 21-09-94
No of invalid logons 2, Last valid logon 04-09-94
The number of valid and invalid logons, and the last invalid logon date,
are statistics that are the same for all users. The last valid logon relates only to you;
it records the last date on which you (or someone using your user account) logged on.
These statistics can be reset from time to time by the Master user.
 
Variations in the logon
sequence
There are some possible variations in the logon sequence, depending on
the details of the security configuration:
There is an optional feature known as Quick Logon. If this feature is enabled, you will
not have to go through the logon sequence every time you want to use the computer.
Instead, the following message is displayed:
Press ALT+L for Logon Sequence
If you press ALT+L within 2 seconds of this message appearing, the logon
sequence is started as described earlier. If you do nothing, you will be automatically
logged-on using a "standard" or "default" user account.
The Master user may have decided to disable the alarm and/or set a null lockout period. If
no lockout period is specified, the system allows unlimited logon attempts.
 
Unattended mode for
Microsoft Windows
An optional enhancement to the security system called LOCSaver ofers an
unattended mode for the Microsoft Windows operating system. When leaving the computer
unattended for a time, you can click the button on your KeyLOC card to obscure the screen
and lock the keyboard and mouse; Windows continues working "behind the scenes".
When you return, another click of the button cancels unattended mode. Ask the Master user
if the computer has this feature.
Remember, if there's anything about the security system you don't understand, ask the
Master user.
 
|


